Crackme - SekaiCTF2024
Summary
Reverse the application --> Discover multiple bad practices in the login implementation --> get the credentials from said bad implementation --> intercept the traffic --> flag
This CTF was part of SekaiCTF2024 reversing category, and was rated 2 stars:
To start we are given an apk. Let’s run it using any emulator, i used Genymotion here:
We can try common credentials but nothing seems to work. All apks are essentially archives, so we can unzip and also decompile the code inside it with a tool like apktool:
apktool d -f -r CrackMe.apk
(d for decompile, -f for force to overwrite destination directory, -r do not decode resources. I went with -r because the binary wouldn't recompile otherwise(and this is a react native app as you will see so we dont need the java code), but you could omit it as patching isnt necessary to complete the challenge.
After decompiling we eventually find what we’re looking for, the logic of the program, in ./CrackMe/assets/index.android.bundle:
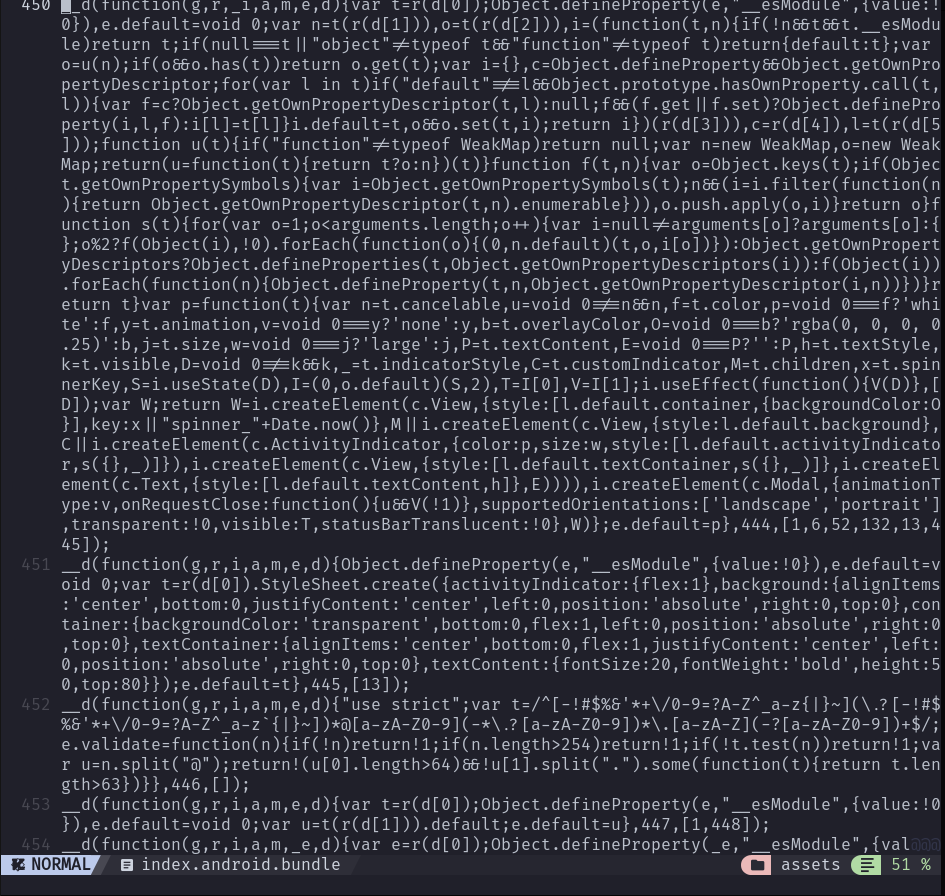
Now I know this could’ve been easier by using a react native deobfuscator, but it was my first time working with this tech so I just went with the javascript deminifier
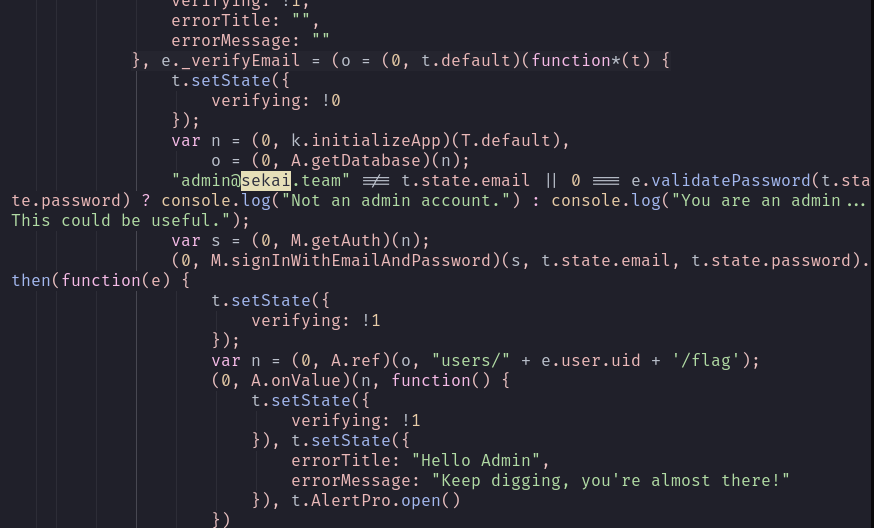
Now, by searching for the keyword sekai we find a valid hardcoded email (very bad practice) as well as the AES encryption key used for passwords and another hardcoded hashed credential (bad cause we have the key)
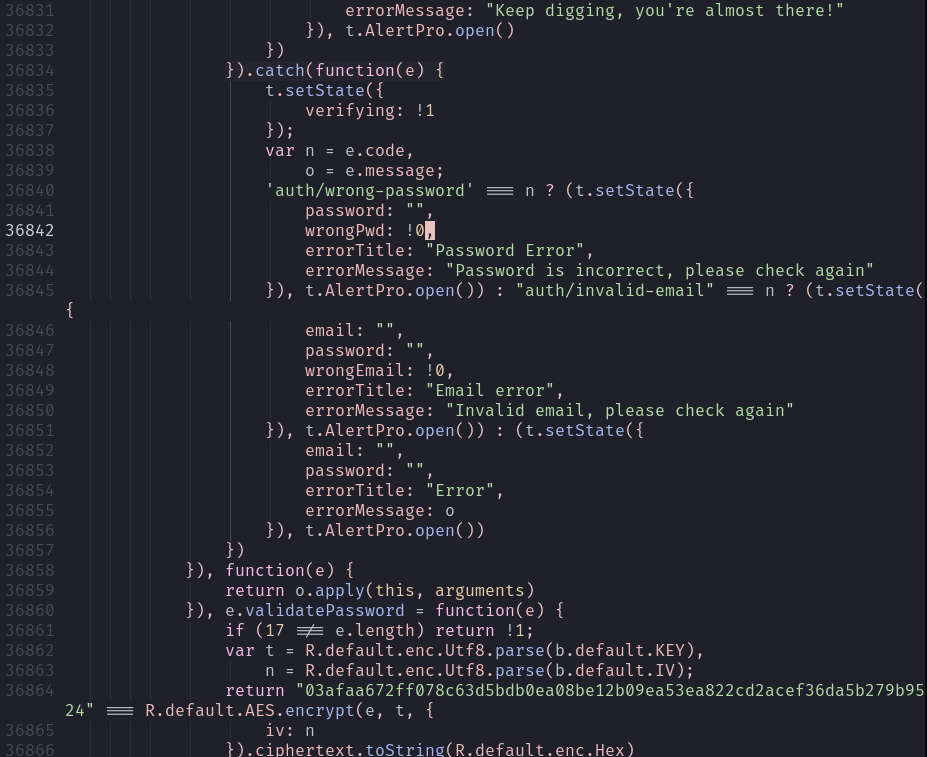
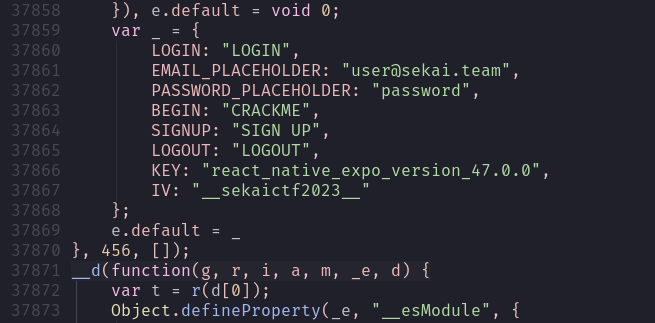
We can now retrieve the original password like so: (Website used)
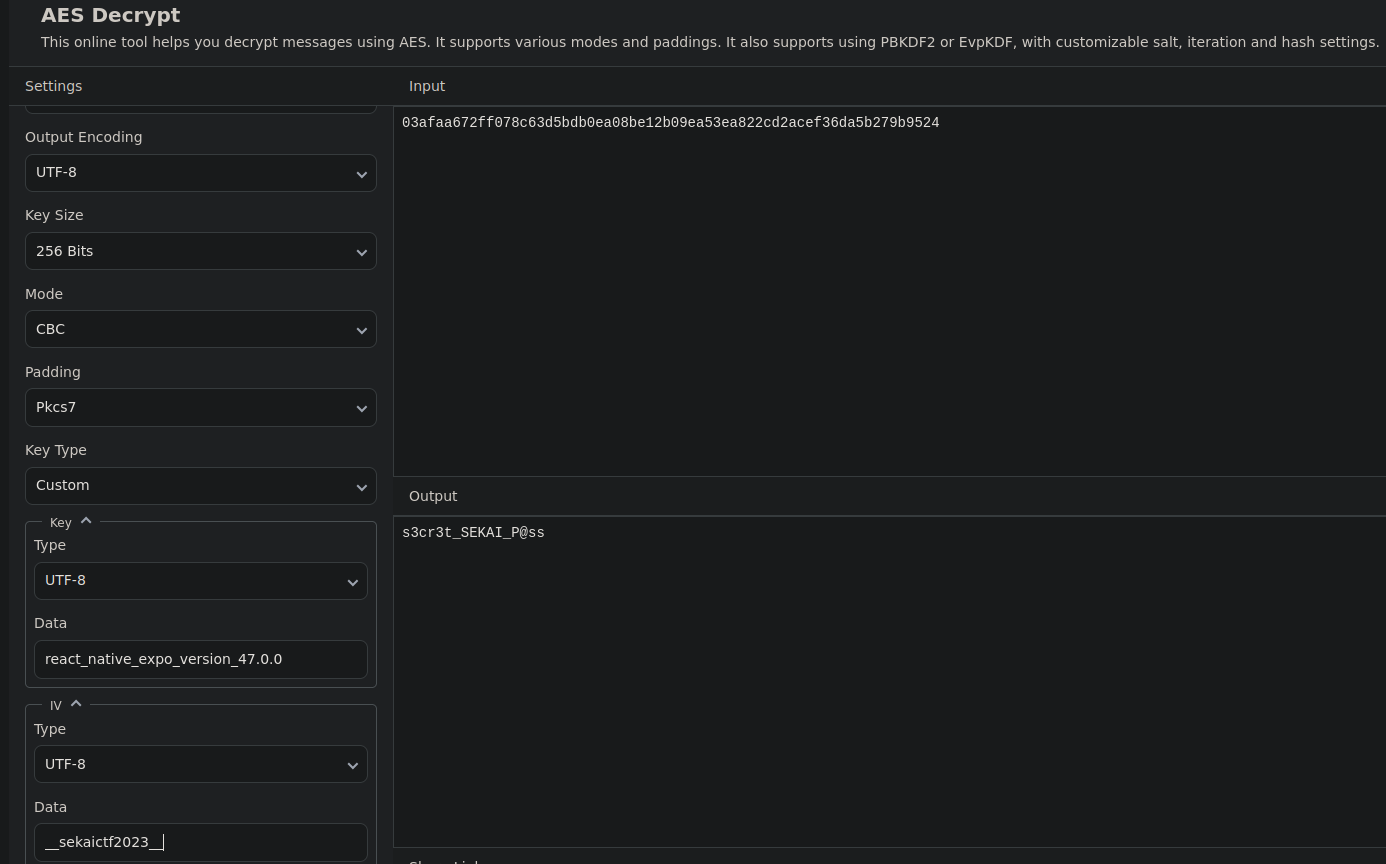
So far we know:
Username: admin@sekai.team
Password: s3cr3t_SEKAI_P@ss
Now lets try these in the app:
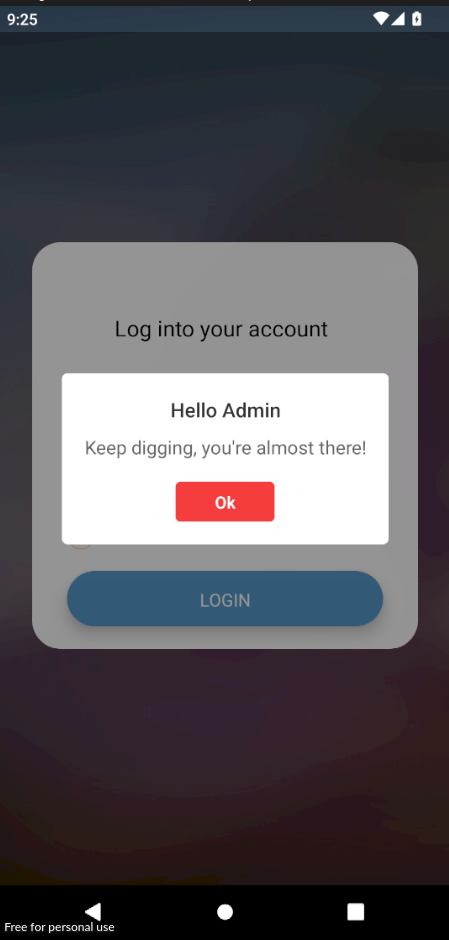
Well thats disappointing, but what I also noticed by scrutinizing the valid login branch of the code, is that when this alert pops up, a request in the background is made to retrieve info from the path /user/ + user.id + /flag.
So our mission now is to intercept that traffic and see what’s happening in the background
Now I won’t go into this in great detail, but the tutorial I followed to get it working is here.
In short, the app uses SSL pinning to make it hard for us to capture the traffic, which means that when the app detects our burp certificate that we use to intercept requests, it stops and doesn’t transmit any data. The solution is to inject javascript code (with something like frida) into the client in such a way that we bypass the certificate pinning:
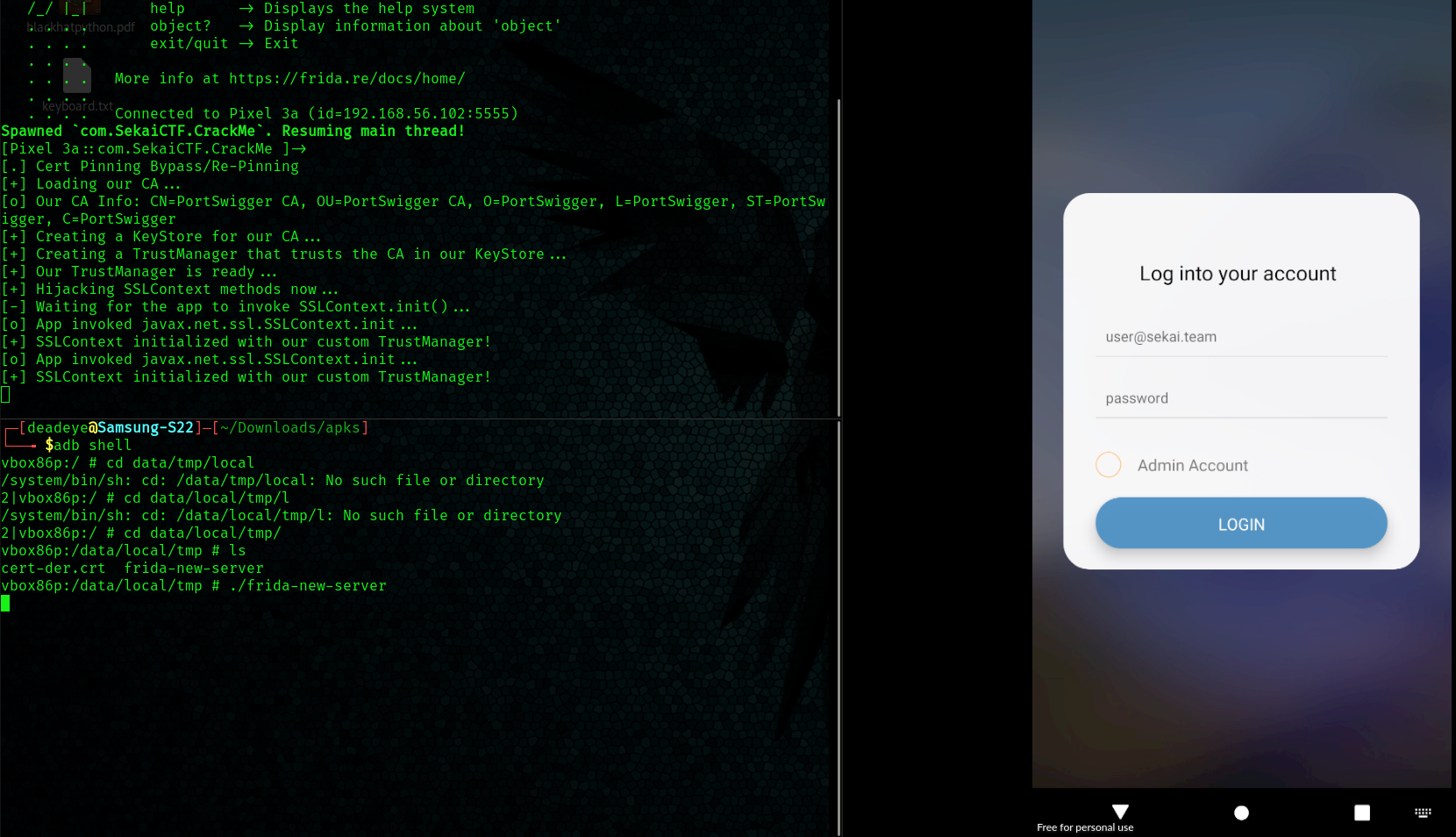
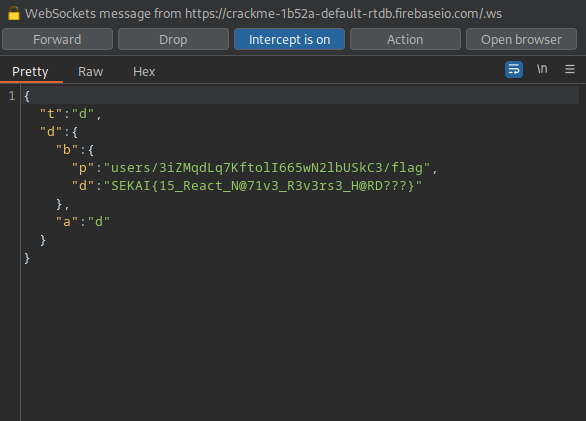
Entering the credentials into the app and turning burps intercept mode on We can see the following conversation:
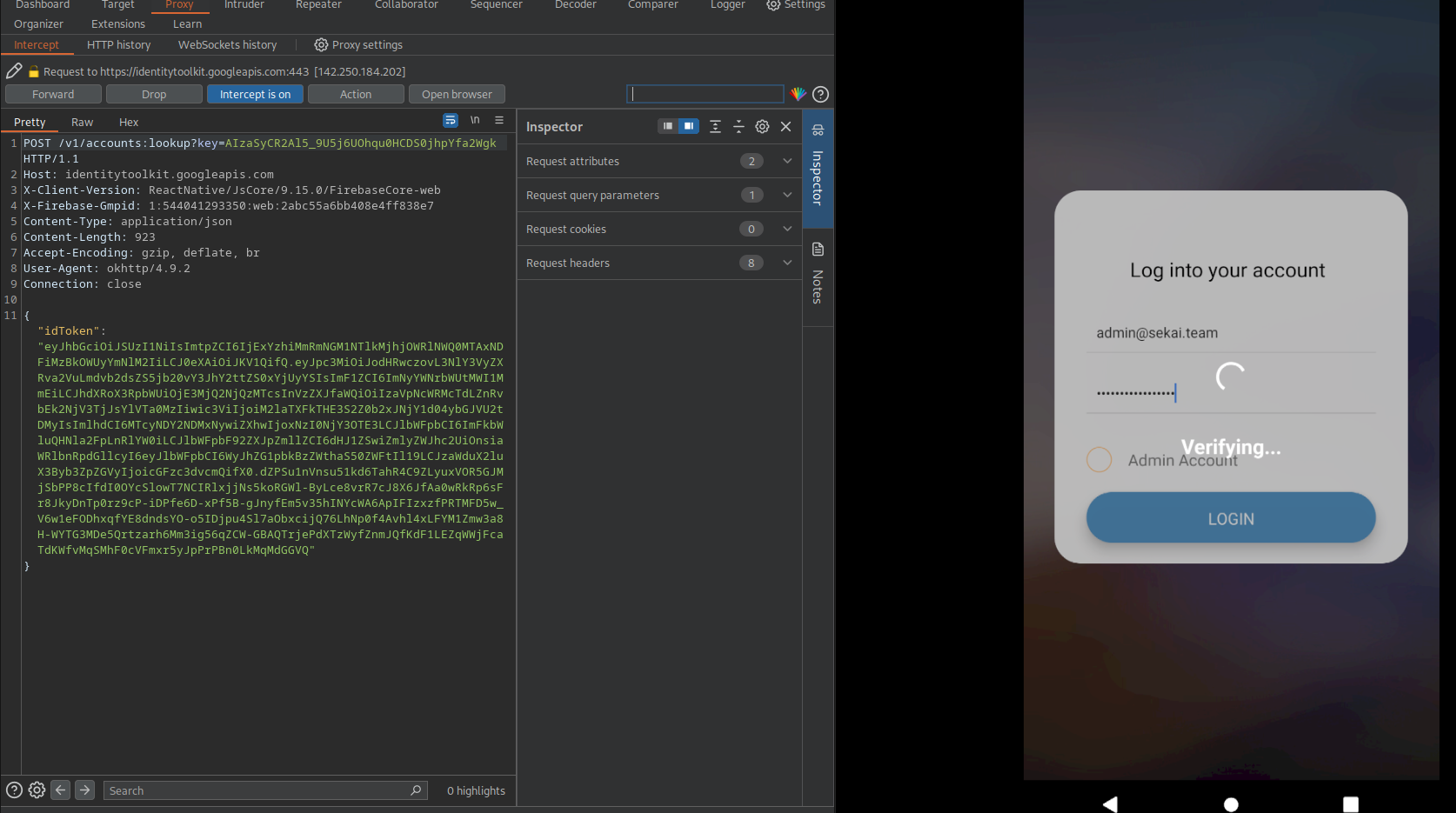
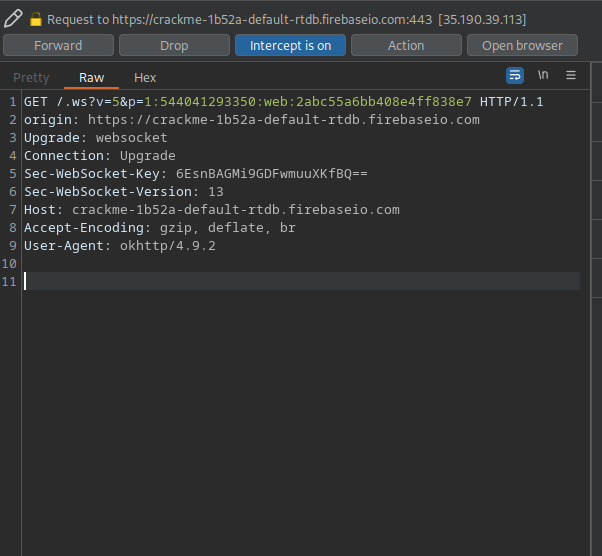
It initiates a websocket connection and then starts requesting data, like the flag:
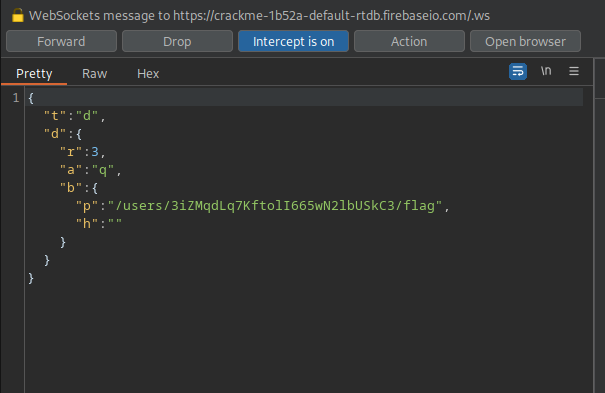
And we get back the flag from the server: